Cyber security project
- For security purpose, the organisation name on this project is changed to xxxx
- security auditing
- penetration testing
- Nmap scanning,
- Wireshark sniffing
- SQL injection
Executive Summary
This project presents the security appraisal (external penetration testing) of xxxx website. In addition, the purpose of the appraisal was to deliver the security evaluation of its current state as well as to provide potential vulnerability and weaknesses.
The Scope of Work
This security evaluation covers penetration testing of one server hosted on 192.168.0.38 address. This assessment was carried out using a black-box testing methodology. For this test, the website and the back-end database were given to the tester group and no other information was been handed on the beginning of the security evaluation or testing process.
Assumption
Through this security appraisal report, we assume the website uses static IP which is considered as localhost IP address, NDA, and rules of engagement have been signed by the tester group and the website provider. As the current information indicates, the company that developed the website is xxxx and the website name is xxxx.
Summary Severity task table

Based on the this information, xxxx website needs to give more attention to data security. In less than half an hour, we were able to get full access to their server. The business needs to invest more resources for the security and integrity of the website. This includes multiple security layer protection to secure the information and resources the organisation(Basta et al., 2014). Network hardening is one of the high risks, which, has been identified in this penetration testing as well as system configuration and security faller. This has to be corrected immediately by implementing layers of security protocols within the system(Basta et al., 2014).
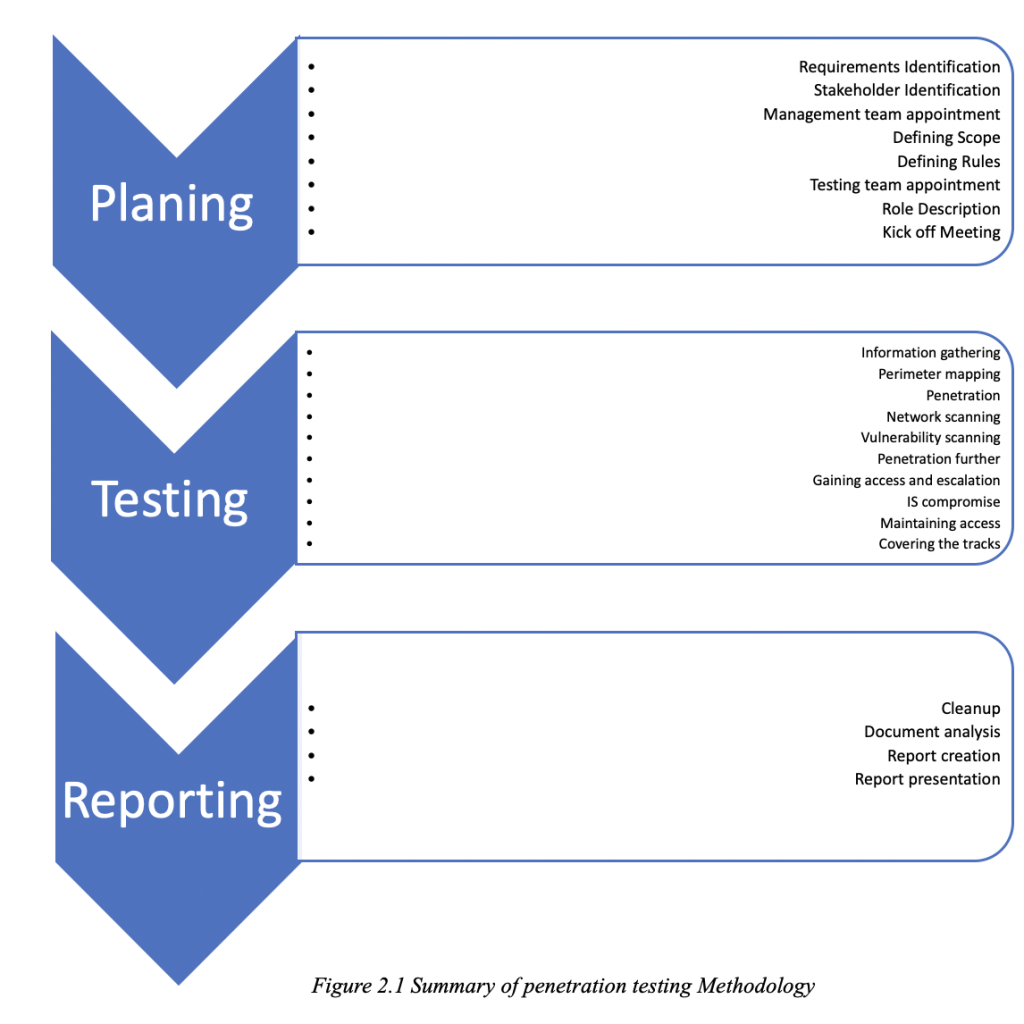
Methodology
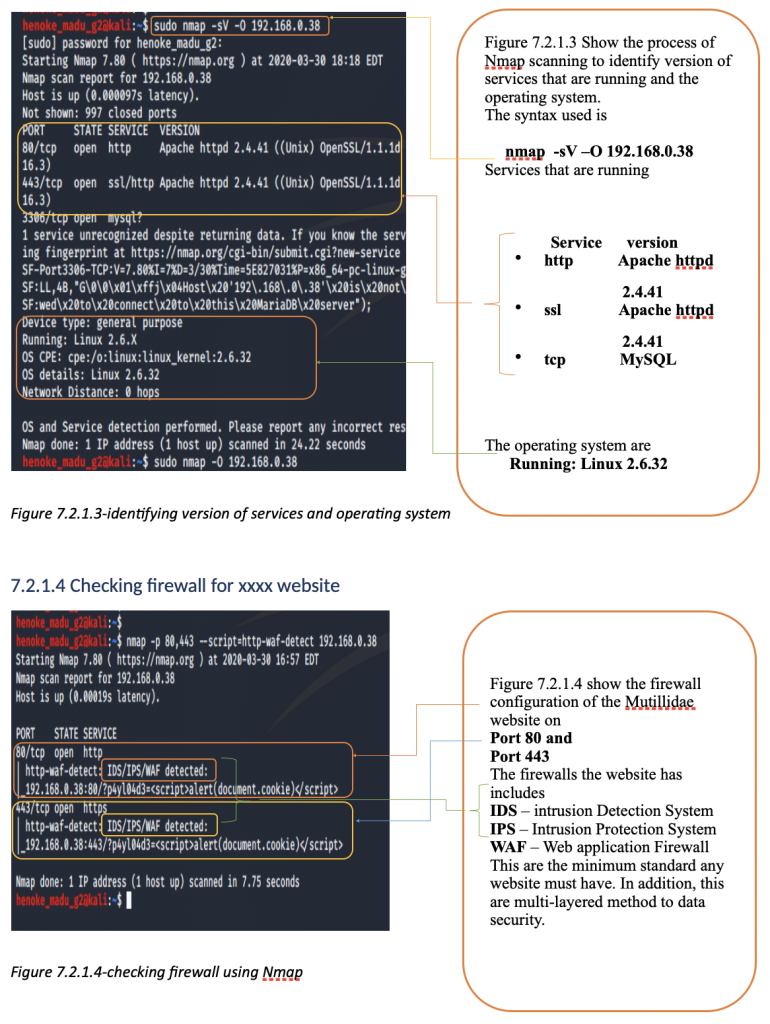
Using nmap
Nmap is the most widely used port scanner. It is used to identify live hosts, scan TCP and UDP open ports, detect firewalls, get versions of services running in remote hosts, and find vulnerabilities. Using Nmap we were able to identify all the services running on the xxxx website,
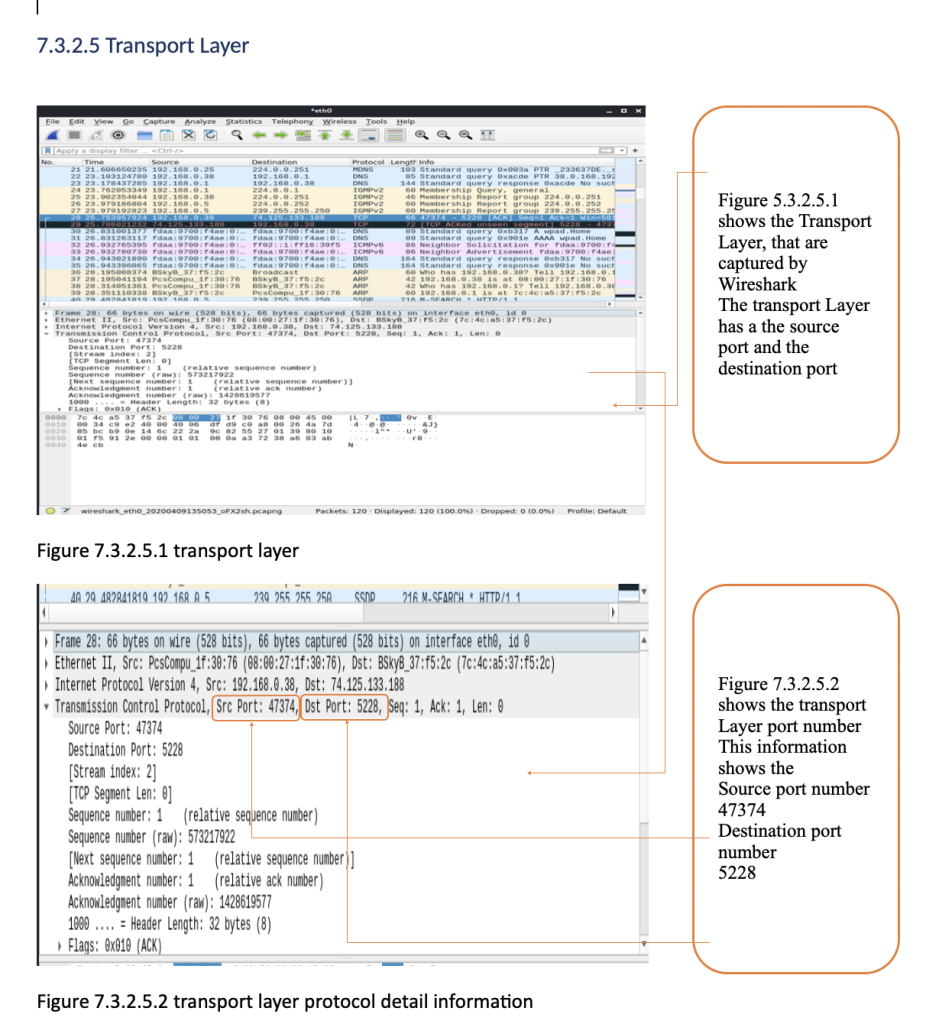
using Wireshark
By using ports, an application can communicate through Transport Layer. Figure 7.3.2.5.2 shows the source port 47374 and destination port 5228 with header length (32 bytes in this case). Each packet will have a different sequence number.
Using Wireshark, we can capture data packet and analyse them in real-time. The main objective of this task is to observe the data traffic in the network. This tool helps the user to monitor the network for errors of any network protocol and network architecture as well as to stop any kind of network attack.
Findings from the penetration test
- xxxx website needs to implement a defence in a depth security mechanism to achieve a better and more secure system.
- We found server 192.168.0.31 protected by a firewall. However, we managed to access the back-end database without any problem. The firewall must be configured for optimal security with,
- Rule-based policy to allow only public services i.e. mail and web access.
- Firewalls anti-mapping rules must be applied
- Only an authorised IP address is allowed to connect to the server and disable all idle services.
- The hosted server runs the services with default configuration such as FTP. xxxx website hosted in 192.168.0.31 is running multiple security vulnerabilities such as SQL injection. A hacker can get access to secure information and manipulate it. xxxx website needs to implement security validation and re-configure firewalls as well as re-design the website components. The suggested approach is a 3-tier design. xxxx website can implement this approach by combining the application server, database server, and firewall. The principle of the process is to separately run the application server from the database server and the connection between can be managed by a firewall.
Summary of Recommendation
- Implementing a defence-in-depth approach is the recommended solution for the xxxx website. This approach will help to secure and protect the information system and its assets.
- Deploy HIPS (Host Intrusion Prevention System) on the user desktop as well as on the server and enable a firewall on all computers.
- Perform security hardening on servers, Networks, and on the internet and external DMZs.
- Configure or setup PMS (patch management systems) to manage or control over all network or system repair, update, and patches to all networks and devices. This can help to increase the security defence mechanism.
- xxxx website needs to implement an input validation system and the website needs to be re-designed.
- Vulnerability assessment must be performed twice a year and penetration testing once a year.
- Implement a training path for IT staff regarding security and firewall configuration approach.
